What to do when your root account in vCenter has been locked out
If the root account is not accessible through the console, the secure shell, and the Virtual Appliance Management Interface (VAMI) (vCenter Server Appliance 5.5 and 6.0 Update 1), the root account has been inactivated due to password expiration or too many fail attempts. To reactivate the root account, the vCenter Server appliance must be rebooted and the kernel option modified in the GRUB bootloader to obtain a root shell.
To reactivate the root account:
1. Reboot the vCenter Server appliance using the vSphere Client.
2. When the GRUB bootloader appears, press the spacebar to disable autoboot.
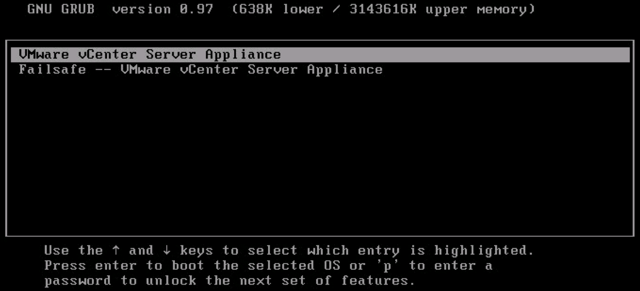
3. Type p to access the appliance boot options.
4. Enter the GRUB password.
Note:
5. Use the arrow keys to highlight VMware vCenter Server Appliance and type e to edit the boot commands.
6. Scroll to the second line displaying the kernel boot parameters.
7. Type e to edit the boot command.
8. Append
9. Press Enter. The GRUB menu reappears.10. Type b to start the boot process. The system boots to a shell.
11. Reset the root password by running the
To reactivate the root account:
1. Reboot the vCenter Server appliance using the vSphere Client.
2. When the GRUB bootloader appears, press the spacebar to disable autoboot.
3. Type p to access the appliance boot options.
4. Enter the GRUB password.
Note:
- If the vCenter Server appliance was deployed without editing the root password in the Virtual Appliance Management Interface (VAMI), the default GRUB password is
vmware. - If the vCenter Server appliance root password was reset using the VAMI, then the GRUB password is the password last set in the VAMI for the root account.
6. Scroll to the second line displaying the kernel boot parameters.
7. Type e to edit the boot command.
8. Append
init=/bin/bash to the kernel boot options.9. Press Enter. The GRUB menu reappears.10. Type b to start the boot process. The system boots to a shell.
11. Reset the root password by running the
passwd root command.12. Restart the appliance by running the reboot command.
Important: Follow the following instructions to prevent future root account lock out when root still active and retain password expiration functionality:
If the root account is still accessible through the vCenter Server appliance console or through the secure shell (SSH), you can prevent this issue from occurring by modifying the /etc/cron.daily/pass-expiration script.
1. Log in to the vCenter Server appliance as the root user.
2. Open the /etc/cron.daily/pass-expiration script using a text editor.
3. Delete these commands:
# disable the password if it's time and not already done.# don't rely on the pam account facility. prepend an x in the shadow file.if [ $TODAY -ge $DEADLINE ] && ! grep -q 'root:x' $SHADOW; then sed -e 's/^root:\(.*\)/root:x\1/' $SHADOW -ifi
4. Enter these commands to replace the forced lockout with a forced password change:
# force a password change for root if we've reached the password expiration date.# pam.unix2 doesn't do this the way we would like, so we do this instead.if [ $TODAY -ge $DEADLINE ]; then chage –d 0 rootfi
5. Save and close the file.
Note: If the root account is locked for long time, it might be due to no space in / because of growth in message log.